This fitness app lets anyone find names and addresses for thousands of soldiers and secret agents

Polar’s widely used fitness app endangers military personnel, intelligence operatives, and people who work at sites where nuclear weapons are stored. It’s dead simple to track down their names and addresses, investigators from De Correspondent and Bellingcat discovered. In total, we found 6,460 individuals across 69 different nationalities.

On Saturday, May 9, 2018, a man takes his regular morning run past the Erbil International Airport in northern Iraq. His pace is leisurely; he covers 2.9 miles in 29 minutes and 34 seconds.
On his wrist is a digital activity tracker, the Polar V800. It records his speed, distance traveled, and calories burned over the course of his run.
The man – let’s call him Tom – is a Dutch soldier, part of the Netherlands’ Capacity Building Mission in Iraq. The CBM is encamped near the Erbil airport. Since 2015, this base has been one of the key locations from which the war against the terrorist group Islamic State is being waged.
We are absolutely not supposed to know who Tom is and where he’s stationed. And we most definitely shouldn’t know where Tom lives.
Yet the activity tracking map in Polar’s fitness app lets us see that many of Tom’s runs start and end near a cluster of homes in a small town in the northern Netherlands. A little Googling gives us his exact address. We also find the names of his wife and children, and photos.
Last Friday, Polar took its user activity map offline and published a short statement* on its website. The company emphasizes that users have consciously chosen to share their activities on the map: the default setting is to keep all workouts private. We asked if this feature has always been opt-in rather than opt-out; the company hasn’t yet answered us. According to Polar, only 2% of its users share workouts on the activity map.
Nevertheless, working with the Bellingcat citizen journalist collective we examined more than two hundred sensitive locations and found 6,460 individuals across 69 nationalities
This enabled us to identify military and intelligence personnel by name, then find out exactly where they and their families live.
The ease with which we learn all this is in stark contrast to the measures the Dutch Ministry of Defense takes to keep its employees safe. To illustrate: only since March of this year may Dutch military personnel board the country’s public transportation system in uniform. Uniformed travel was forbidden in 2014, after a Dutch jihadist in Syria threatened to attack the government.
The ministry also enforces stringent rules to keep the identities of intelligence and special forces personnel confidential. The names and addresses of intelligence operatives are state secrets. The government’s policy for deployed military personnel is also strict. Dutch soldiers on a mission – such as the Capacity Building Mission in Iraq, where Tom takes his runs – may only address each other by first name.
A spokesperson for the Dutch defense department explains why: if the identities of these high-risk groups are exposed, not only are these soldiers in danger, but also the entire operation and the Netherlands’ national security. Many other countries enforce similarly stringent rules. In the US, for example, sharing an intelligence agent’s identity is punishable by up to ten years in prison.
Yet we still found the names and addresses of personnel at intelligence agencies including the NSA and Secret Service in the US, the GCHQ and MI6 in the UK, the GRU and the SVR RF in Russia, the DGSE in France, and the MIVD in the Netherlands.
We found the names and addresses of personnel at military bases including Guantánamo Bay in Cuba, Erbil in Iraq, Gao in Mali, and bases in Afghanistan, Saudi Arabia, Qatar, Chad, and South Korea.
We also learned the names and addresses of personnel at nuclear storage facilities, maximum security prisons, military airports where nuclear weapons are stored, and drone bases.

We found this information not through hacking or some other technological wizardry, but through a little clever searching in the online map that Polar makes available to anyone with an account. That map displays every run, bike ride, and swim its users have logged since 2014. Anyone with a basic understanding of computers and some common sense can find this information.
Here’s how we pinpointed home addresses:
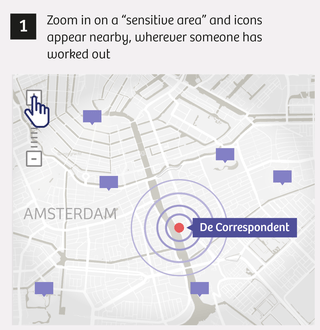
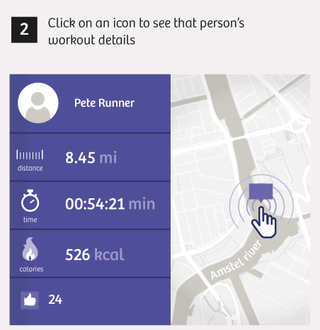
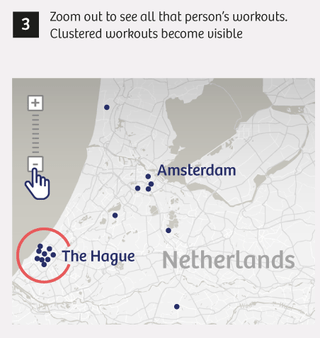
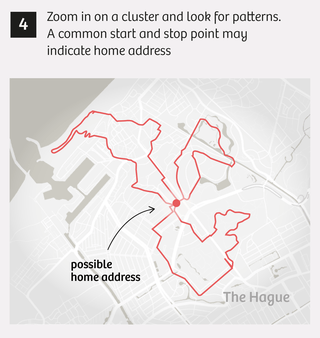
Simple searching is how we were able to find 6,460 users who have tracked their sports activities at or near sensitive locations like those above since 2014. Of these users, nearly 90% list a name and city on their profile page, which makes finding their home address significantly easier.
Some users wisely hide behind a private profile, but an oversight in the Polar app allowed us to uncover the exerciser’s identity nonetheless in most cases. That’s how we found the names and addresses of employees at the NSA, the MIVD, and the GRU.
Another oversight in Polar’s technology is the lack of a limit on how much information you can request. For example, we were able to automatically call up every activity across the entire world for those 6,460 users, which made it much easier to determine their home address, where people’s workouts often begin and end.
That means the names and addresses of the world’s soldiers and secret agents are there for the taking. We informed the Dutch Ministry of Defense two weeks ago. The ministry has assisted us in alerting foreign ministries and intelligence agencies.
The ministry has also promised it will soon draft a plan to prohibit the use of fitness apps on personal devices and technology such as wearables for “specific employees under specific circumstances.”
The ministry has already physically disabled the use of these apps on the telephones it provides to its employees. All personnel have since been “informed of the dangers” of using sports and fitness apps and “associated wearables.”
This incident is not an isolated one. In January, the Strava fitness app made the news when military analysts discovered the company’s online activity tracking map was detailed enough to track down the location of military bases.
For this investigation, we also tested the popular apps Strava, Runkeeper and Endomondo. Though it’s harder to identify people and find their home addresses than it is through Polar, we were ultimately able to do so using these apps. In contrast to Polar’s app, there is no indication that people whose profiles are set to private can also be identified in these apps. We informed them of our findings last week.
Conclusion
“This example demonstrates how important it is to be aware of all the consequences digital technology can have,” said the Dutch minister of defense, Ank Bijleveld, in response to our investigation. “Technology keeps making more and more things possible, but the flip side of that ability is adjusting our security and awareness to match.”
It’s good news that the minister recognizes the severity of the problem. But this isn’t the first time she’s promised improvement. After the Strava incident last January, the Ministry of Defense alerted all its personnel. Our investigation also examined Strava. Finding users’ names and addresses wasn’t as easy as it was in Polar – but find Strava’s users we did. Including soldiers and secret agents.
All names in this article have been changed. Translated from Dutch by Grayson Morris and Rufus Kain. The original articles in Dutch can be found here.
All our coverage in English can be found below.



